Privacy risks in Data Collection and Storage
Are there privacy risks in online data collection and storage? To put it simply, yes. But what kind of risks are there? Privacy risks in online data collection and storage include an invasion of privacy, invasive surveillance, and even misuse of user data. Users often are unaware about these privacy risks, which violate laws. Many malicious things can be done with online data collection and storage. In case you don’t know much about invasion of privacy, invasive surveillance, or misuse of user data, I’ll explain it real quickly. Invasion of privacy is essentially when a user/company intrudes in on an individual’s private life and/or information. Invasion of privacy is related to misuse of user data because of the fact that the user/company intruding on an individual’s personal life/information can misuse that information. This information can be sold to other companies without the user’s consent, and even using the user’s information for the user/company’s own gain. Invasion of surveillance is essentially when a user/company monitors an individual’s activities without the individual’s consent. To protect user information, companies conduct risk assessments, enforce security policies, and use encryption to protect sensitive information, along with much more. They also store user information in safe and secure locations. Some companies also try to limit the amount of personal data they collect, as well as anonymizing information in case of a breach. Zoom, an app we all used, intruded on their user’s information, and misused that information, by giving it to third party companies, one being Facebook, without the user’s knowledge or consent. However, Apple is known for its user privacy, as they employ end to end encryption to protect user messages and data. Additionally, Apple regularly releases security updates to enhance the protection of user information.
Misuse and Protection of Computing Resources
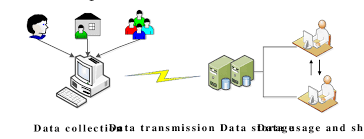
Computing resources such as wifi and computers can be misused, but how exactly does it happen? Computing resources like wifi can be exploited in many ways, leading to security risks and data breaches. But how are these resources exploited? Well, these resources are exploited through vulnerabilities in software and hardware, among other things. But what kind of risks are there? Well, risks include malware infections and software vulnerabilities. An example of this happened in 2019 when Capital One’s servers were hacked, and the personal information of over 100 million users were exposed. The personal information stolen included stolen social security numbers, bank details, and credit scores. To keep computing resources safe, businesses use security measures like regular software updates, strong passwords, multi factor authentication. Firewalls and antivirus programs also help to stop threats before any harm is caused. Regular updates keeps hackers from exploiting advantage of outdated software. Strong passwords make it harder for attackers to break into accounts. These steps are important for protecting sensitive information. Without them, computing resources would be even more at risk. Data misuse is another big problem, but how does it happen? Data misuse usually occurs when insiders steal information. Private information can be put at risk if stored on unsafe devices with unsafe security measures, or shared with people who aren’t supposed to have access. For example, in 2022, a Cash App employee downloaded private financial records of 8 million users, resulting in a huge privacy breach. But how can companies prevent this? Well, companies can monitor user activity, and take action if something suspicious occurs. By doing this, companies can protect sensitive data and avoid security breaches.

Unauthorized Access to Information
Computing resources such as wifi and computers can be misused, but how exactly does it happen? Computing resources like wifi can be exploited in many ways, leading to security risks and data breaches. But how are these resources exploited? Well, these resources are exploited through vulnerabilities in software and hardware, among other things. But what kind of risks are there? Well, risks include malware infections and software vulnerabilities. An example of this happened in 2019 when Capital One’s servers were hacked, and the personal information of over 100 million users were exposed. The personal information stolen included stolen social security numbers, bank details, and credit scores. To keep computing resources safe, businesses use security measures like regular software updates, strong passwords, multi factor authentication. Firewalls and antivirus programs also help to stop threats before any harm is caused. Regular updates keeps hackers from exploiting advantage of outdated software. Strong passwords make it harder for attackers to break into accounts. These steps are important for protecting sensitive information. Without them, computing resources would be even more at risk. Data misuse is another big problem, but how does it happen? Data misuse usually occurs when insiders steal information. Private information can be put at risk if stored on unsafe devices with unsafe security measures, or shared with people who aren’t supposed to have access. For example, in 2022, a Cash App employee downloaded private financial records of 8 million users, resulting in a huge privacy breach. But how can companies prevent this? Well, companies can monitor user activity, and take action if something suspicious occurs. By doing this, companies can protect sensitive data and avoid security breaches. There are a variety of methods that hackers use to gain unauthorized access to information, but how? Some methods include phishing, malware, and exploiting software vulnerabilities. In case you don’t know a lot about the methods listed above, I’ll explain it real quickly. Phishing is when a hacker tricks someone into sharing their personal information by pretending to be a someone else. Malware is a type of software that hackers use to damage/take control of a system. Exploiting software vulnerabilities is essentially taking advantage of weaknesses in a system to gain unauthorized access. What are data breaches? Data breaches are when a hacker accesses information without being allowed to. Data breaches usually occur because of weak passwords, outdated software, and phishing attacks. Hackers target company's information for a variety of reasons, but mainly do so because any information hacked can be sold. Because of this, companies must take many steps in protecting information from hackers to prevent data breaches. To protect information from hackers, companies will use encrypted data, two factor authentication, and strong passwords. 2 factor authentication is a security method, requiring someone to go through at least 2 levels of authentication to access information. Additionally, encrypted data is when information is transformed into a form of unreadable text, only allowing the company to see the readable text.


Benefits and Risks of Computing Innovations
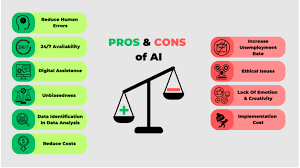
As artificial intelligence becomes more advanced, and offers more and more advantages everyday. Artificial intelligence can perform almost any action in a short amount of time, ranging from helping one understand a concept, to writing a book. For example, AI models such as ChatGPT can create in-depth explanations of complex concepts and problems, translate languages, and even code! This allows for individuals using AI to access information and complete tasks in no time. Despite artificial intelligence’s many up-sides, it does have its down-sides. Artificial intelligence creates vulnerabilities such as over-reliance on artificial intelligence, which can lead to a decline in critical thinking skills. Additionally, artificial intelligence can be exploited for malicious reasons, as it has been used to help plan and create an IED used to blow up a Cybertruck. Finally, as artificial intelligence is trained more, it’s potential to impersonate one is greatly increased. Artificial intelligence can take in information from the web extremely quickly, including videos, social media, and news outlets. Using this information, AI can make highly realistic voice recordings, videos, and images. These highly realistic fakes can then be used to phish someone into doing something, such as giving up personal information.